The Unseen Chaos
Orchestrating enterprise security and onboarding for 4,000 contractors by unifying 3 fragmented systems into a single source of truth.
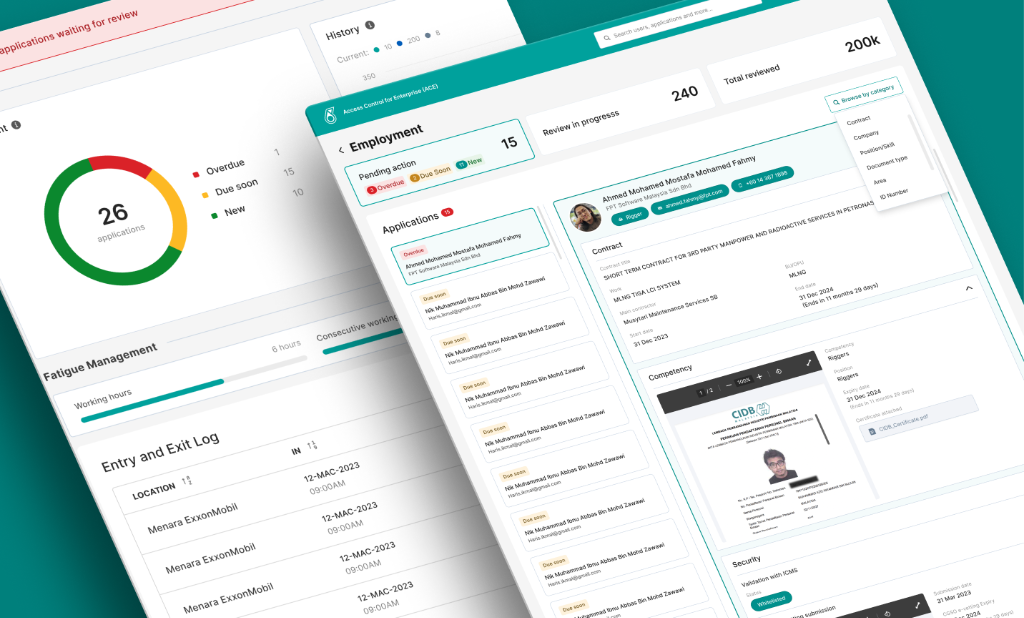
The Friction & The Stakes
The Bottleneck
A massive critical maintenance period required 4,000 additional contractors. The existing 14-step manual workflow across 3 systems (XPRESS, EPASS, CRIS) paralyzed operations.
Bureaucratic Dogma
Security was equated with "hard to use". I had to visualize the unseen chaos to leadership, reframing that when users bypass systems to get work done, security fails.
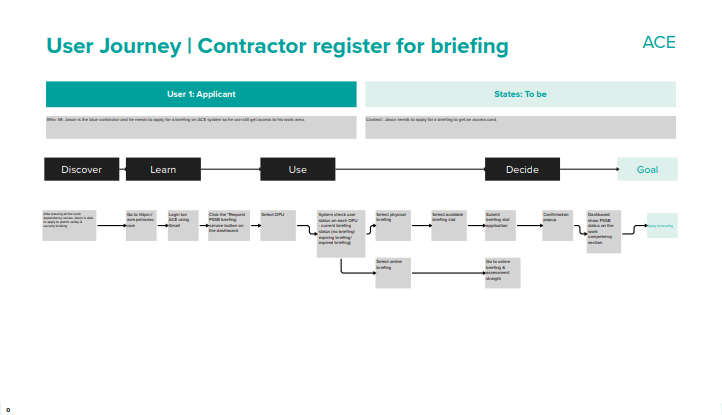
The ACE Solution
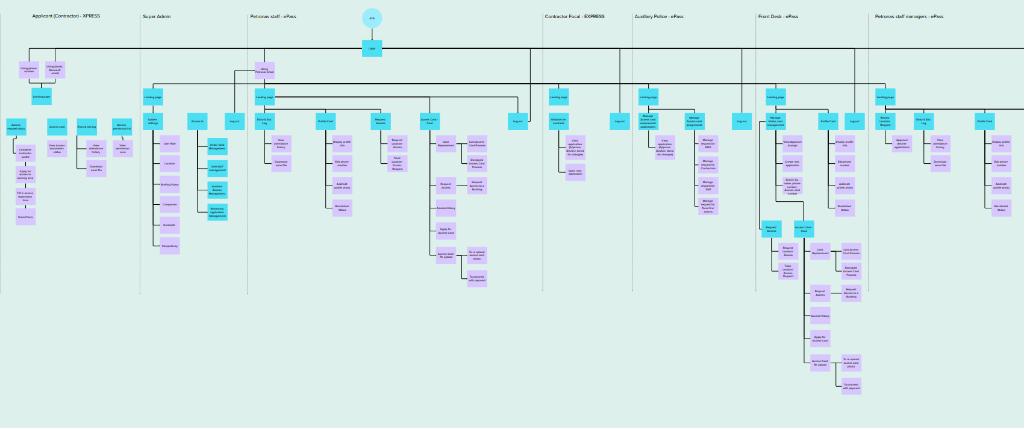
Unified Information Architecture
Consolidated data models from legacy systems into a single entity relationship. This created a "Single Source of Truth" that eliminated redundant data entry and synchronization errors.
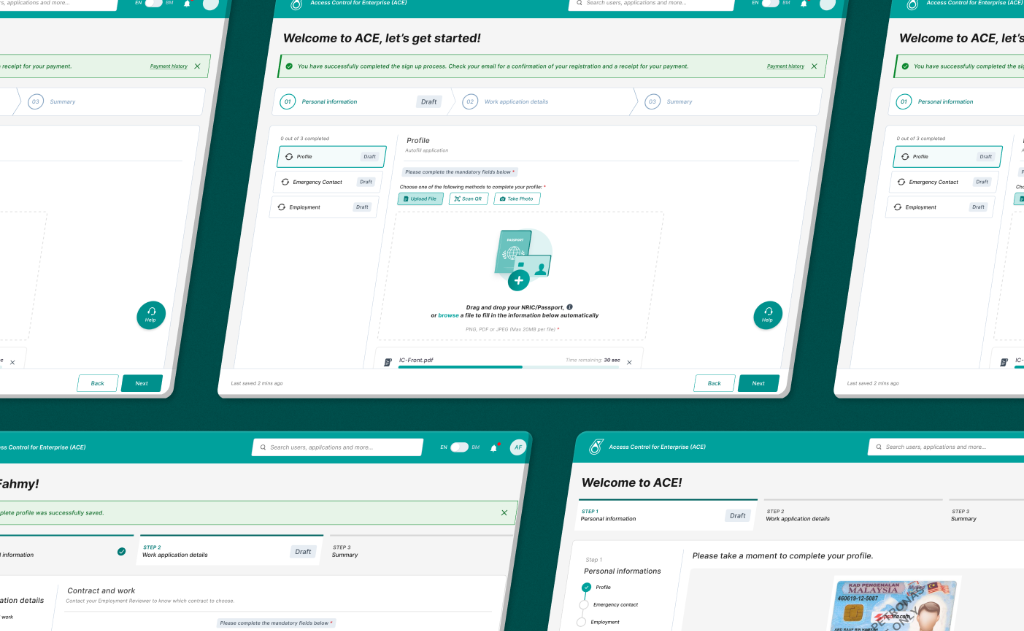
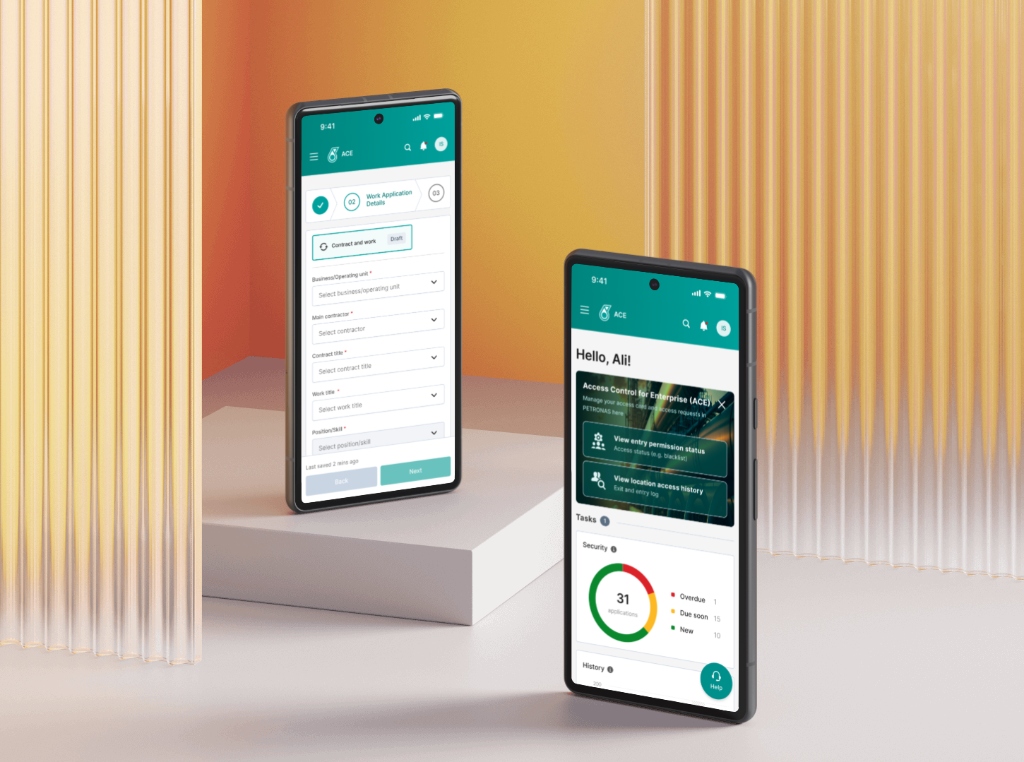
Streamlined Onboarding
We deconstructed the complex registration process into a simple, step-by-step wizard. By breaking forms into digestible chunks and providing clear progress indicators, we reduced data entry errors and user abandonment.
Mobile-First Self-Service
The "Friction Killer". Shifted data entry from bottlenecked administrative focal points to the 50,000 users themselves via a mobile portal. Enabled access anywhere, removing physical queues at the gate house.
Outcomes & Impact
40% Faster Onboarding
Drastically reduced approval timelines by decentralizing data entry and automating validation checks.
Crisis Ready
Operational scalability ensured the facility could handle the 4,000 contractor surge without security compromises.
Data Integrity
Established a unified single source of truth, enabling real-time reporting and accurate compliance tracking.
"The most dangerous security vulnerability isn't a weak firewall—it's a process so complex that people bypass it to get their job done."